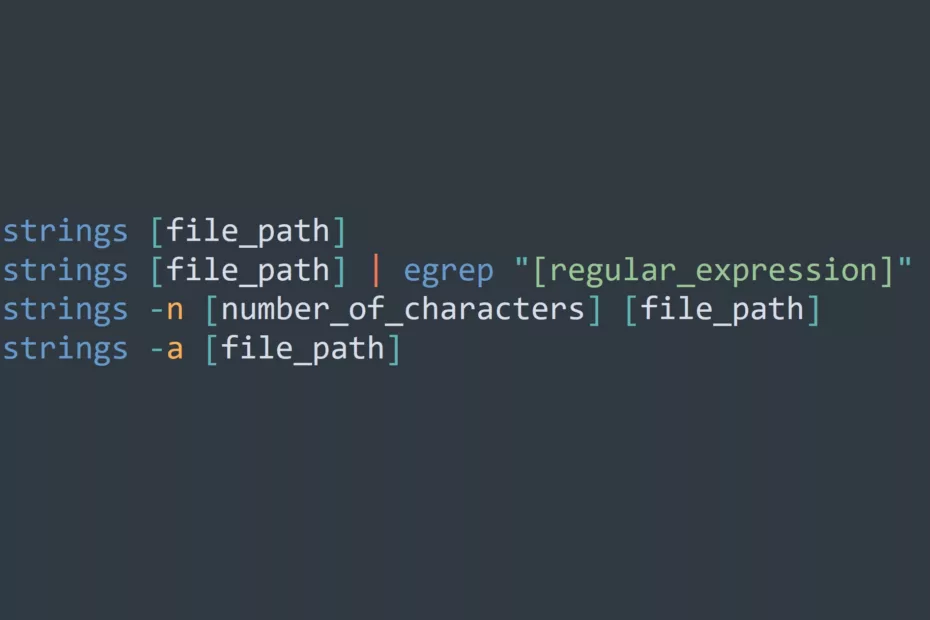
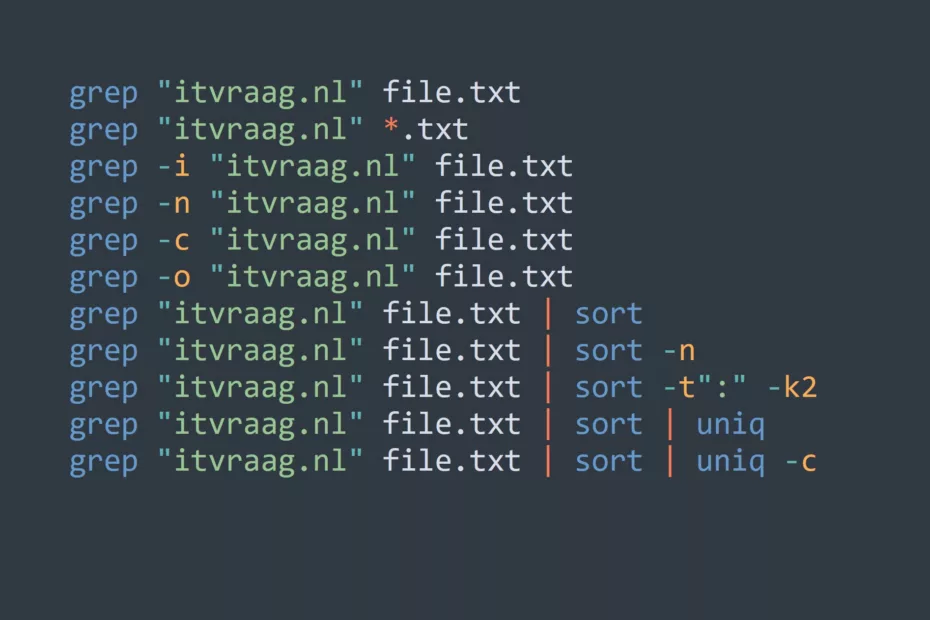
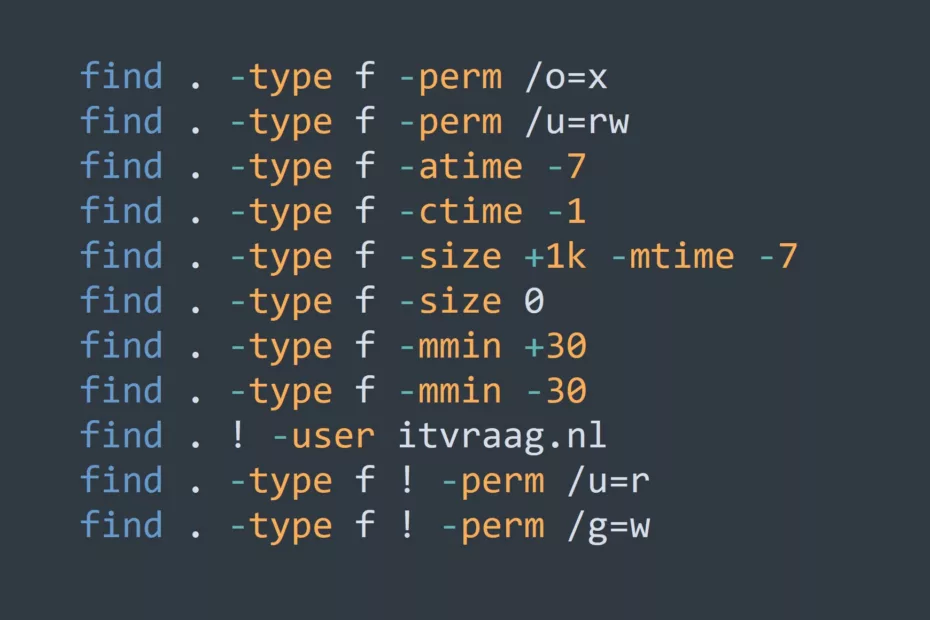
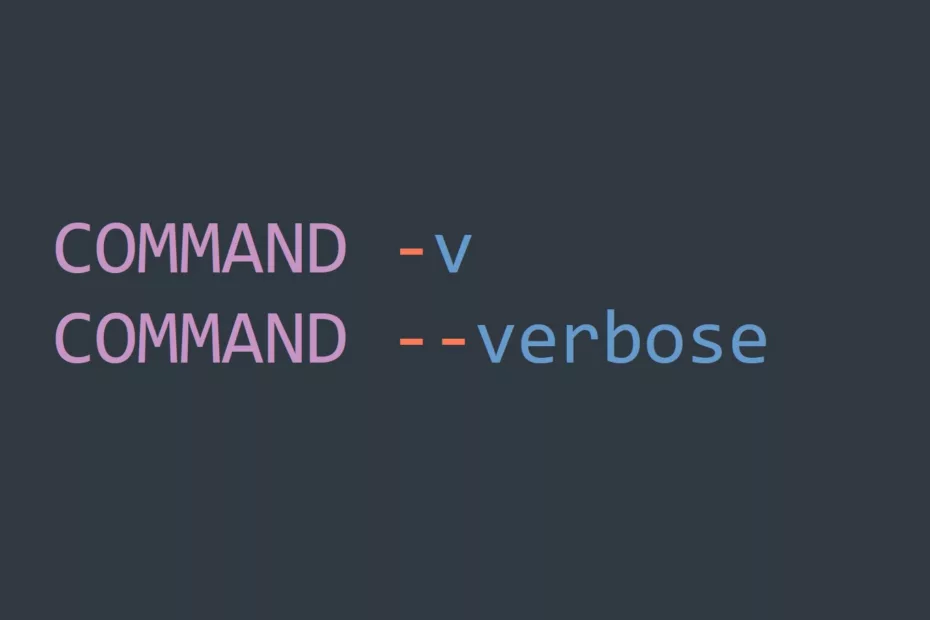
Who’s On Your Network? Best Practices for Managing WiFi Access for Visitors
Why Should You Limit or Remove WiFi Access to Visitors? Security Concerns Providing WiFi access to visitors also means exposing your network to potential security threats. Visitors may inadvertently or intentionally download malware or engage in unauthorized activities that can compromise your network’s security. This is particularly concerning if you’re… Read More »Who’s On Your Network? Best Practices for Managing WiFi Access for Visitors