TLDR; This blog explored the key concepts of risk management in IT, including risk identification, analysis and evaluation, treatment and response, and monitoring and review. IT professionals must identify and assess potential risks in order to develop a risk treatment and response plan. Once the plan is implemented, it should be monitored and reviewed regularly. By staying up-to-date with the latest tools, techniques, and best practices in risk management, IT professionals can help their organizations stay ahead of potential risks and maintain a competitive edge in the digital economy.
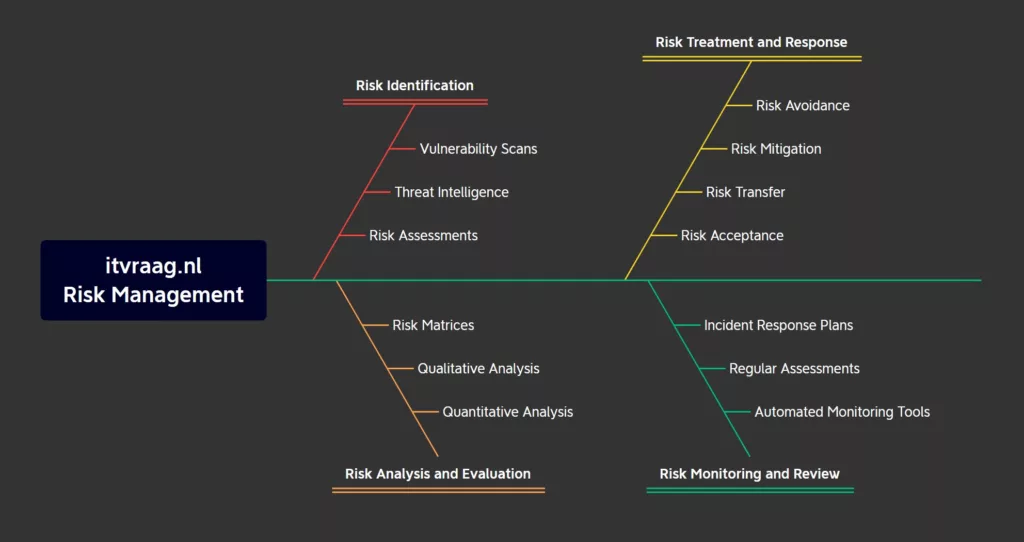
I. Risk Identification
The first step in risk management is identifying and assessing potential risks. In the context of IT, risks can include everything from software vulnerabilities and data breaches to natural disasters and human error. To identify risks, IT professionals can use a variety of tools and techniques, such as:
- Vulnerability scans: These scans identify weaknesses in an organization’s IT infrastructure and systems, such as outdated software, misconfigured servers, or unpatched security holes.
- Threat intelligence: This involves gathering information about potential or actual cyber threats and risks to an organization, which can help IT professionals identify and prioritize potential risks.
- Risk assessments: These assessments evaluate the likelihood and potential impact of different risks to an organization’s technology infrastructure and operations.
II. Risk Analysis and Evaluation
Once potential risks have been identified, the next step is to analyze and evaluate them. This involves determining the likelihood of a risk occurring and the potential impact it could have on an organization’s technology infrastructure and operations. IT professionals can use a variety of methods to analyze and evaluate risks, such as:
- Quantitative analysis: This involves using numerical data to evaluate the likelihood and potential impact of different risks.
- Qualitative analysis: This involves using subjective criteria, such as expert opinion and experience, to evaluate risks.
- Risk matrices: These matrices can help IT professionals evaluate the likelihood and potential impact of different risks based on predefined criteria.
III. Risk Treatment and Response
After potential risks have been identified and analyzed, the next step is to develop a risk treatment and response plan. This involves determining how to respond to each risk, based on its likelihood and potential impact. Some possible risk treatment options include:
- Avoidance: This involves taking steps to eliminate or reduce the risk, such as by not using a particular software or service that has a known vulnerability.
- Mitigation: This involves taking steps to reduce the likelihood or impact of a risk, such as by implementing security controls or backups.
- Transfer: This involves transferring the risk to another party, such as by purchasing insurance.
- Acceptance: This involves accepting the risk and developing a plan to mitigate its potential impact, such as by developing a disaster recovery plan.
IV. Risk Monitoring and Review
The final step in risk management is to monitor and review risks on an ongoing basis. This involves tracking risks and evaluating the effectiveness of risk responses, as well as identifying new risks as they arise. IT professionals can use a variety of tools and techniques to monitor and review risks, such as:
- Automated monitoring tools: These tools can help IT professionals track changes in their IT infrastructure and systems, such as changes in software versions or new security threats.
- Regular assessments: Regular risk assessments can help IT professionals identify new risks and evaluate the effectiveness of existing risk responses.
- Incident response plans: These plans can help IT professionals respond quickly and effectively to security incidents or data breaches, minimizing their impact on the organization.