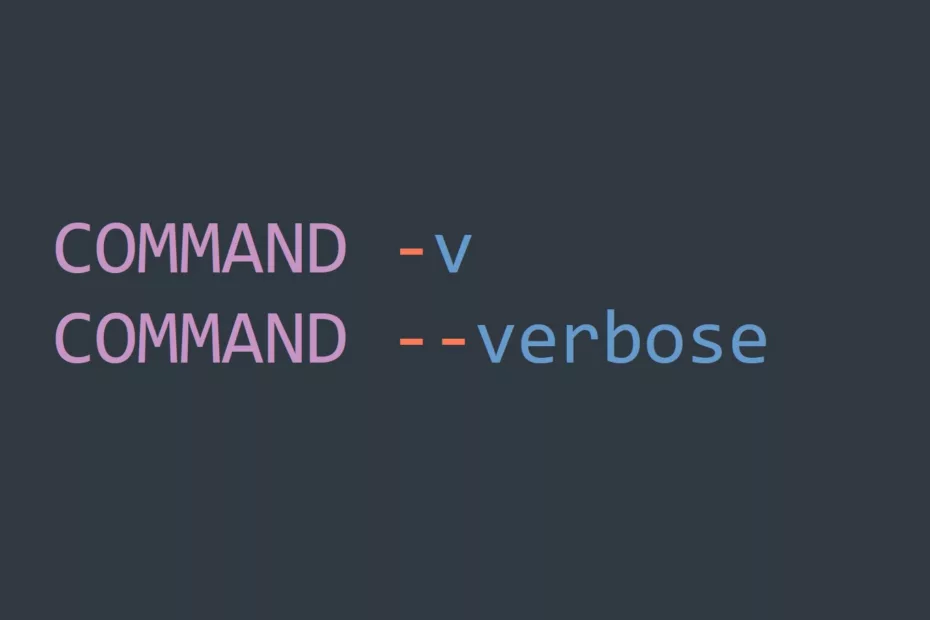
Bash Script Tutorial: Learn the Fundamentals of Variables, Redirection, and Loops
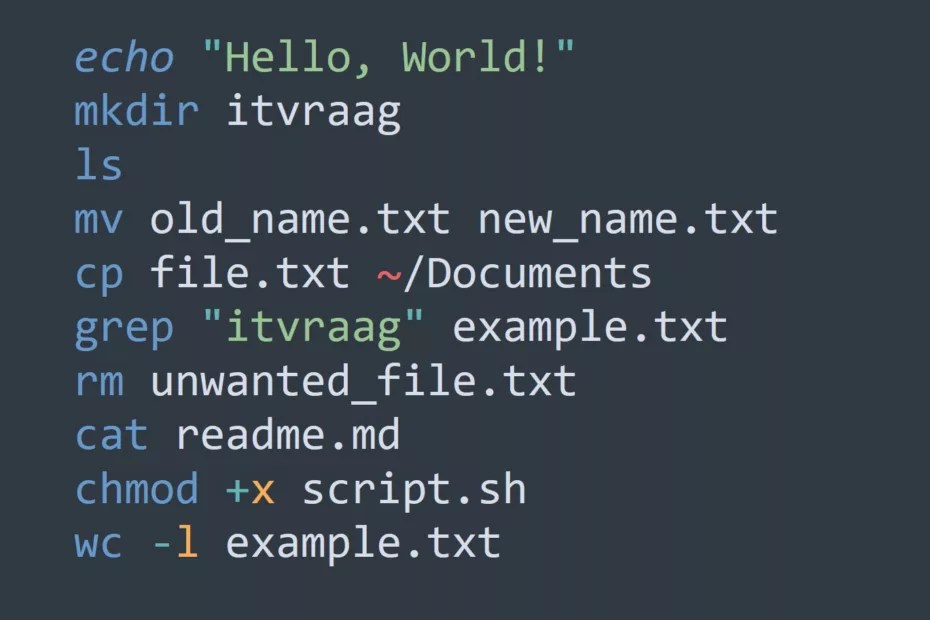
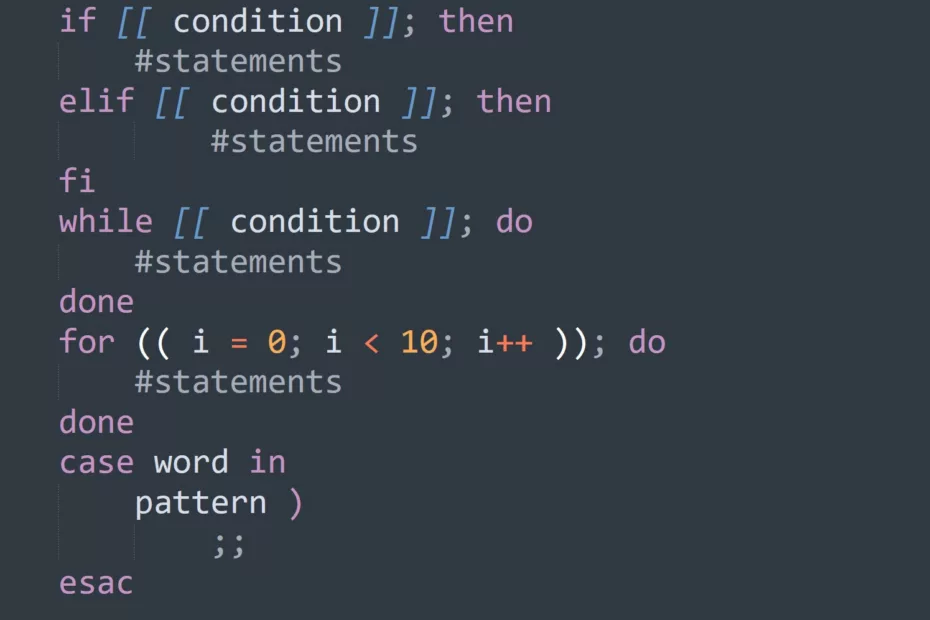
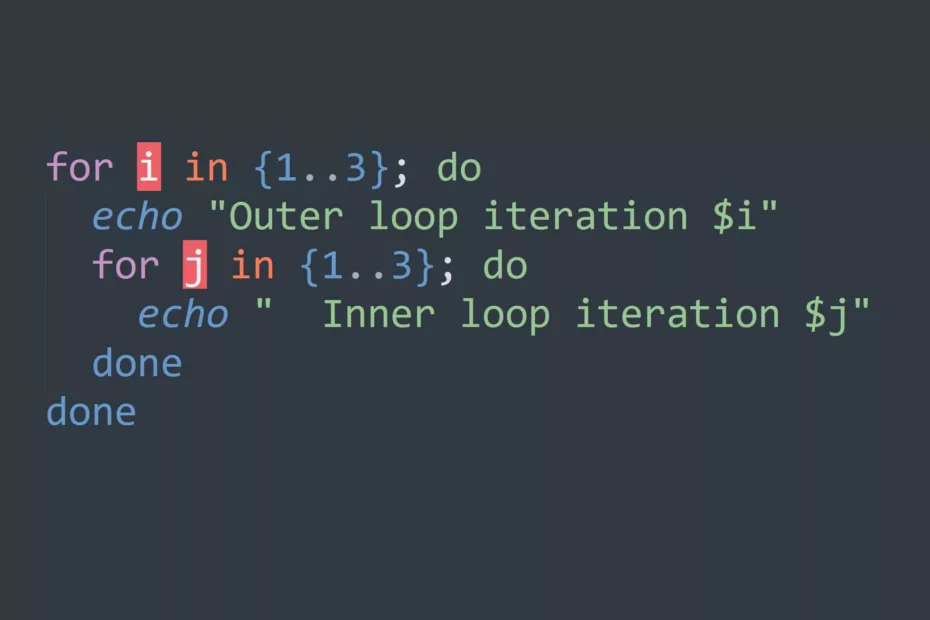
In this comprehensive tutorial, we will cover everything you need to know to get started with bash scripting. From basic commands to complex conditionals, we’ll walk you through everything you need to know to streamline your workflow and save time. Bash Basics Terminal vs Shell vs Bash: What’s the Difference?… Read More »Bash Script Tutorial: Learn the Fundamentals of Variables, Redirection, and Loops