Want to Find Hidden Strings in Your Binary Files? Try the Strings Command in Linux
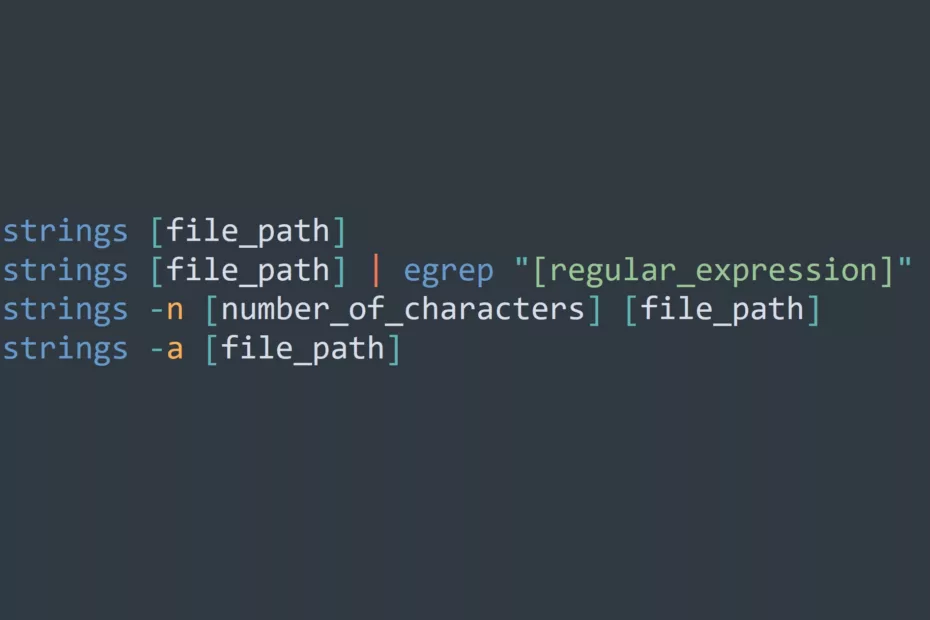
The Linux “strings” command extracts readable text from binary files, enabling users to search for strings in files, filter the output using regular expressions, and perform a recursive search for strings across multiple files. The command is easy to use and comes with options and flags that can be combined… Read More »Want to Find Hidden Strings in Your Binary Files? Try the Strings Command in Linux