Basics & Practical Tips of DHCP
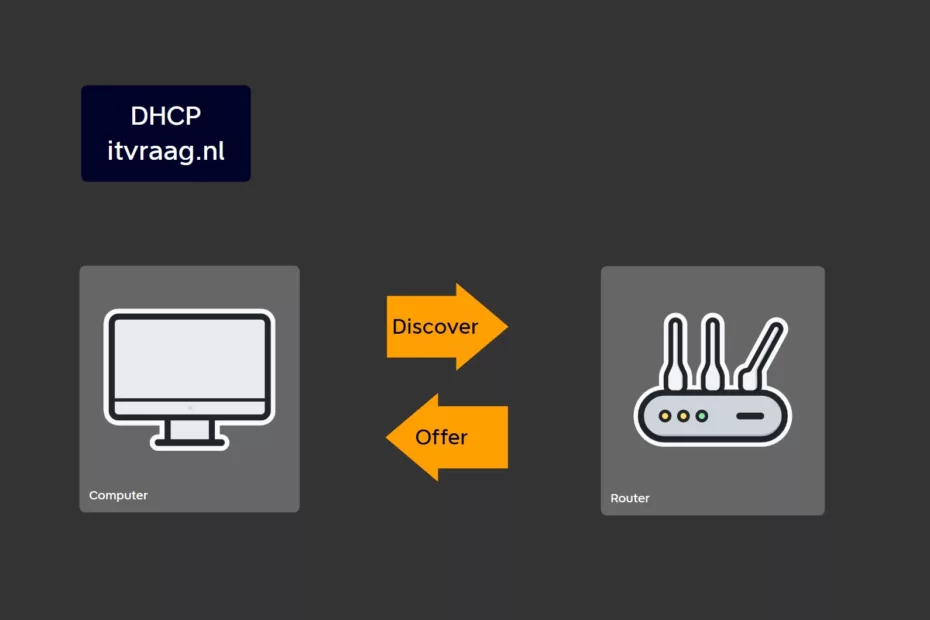
TLDR; DHCP (Dynamic Host Configuration Protocol) automatically assigns IP addresses to devices on a network, removing the need for manual configuration. It enables communication and internet access. This blog explores basics, importance, and practical tips (using dedicated server, configuring reservations, monitoring logs, and testing). What is DHCP? DHCP is a… Read More »Basics & Practical Tips of DHCP