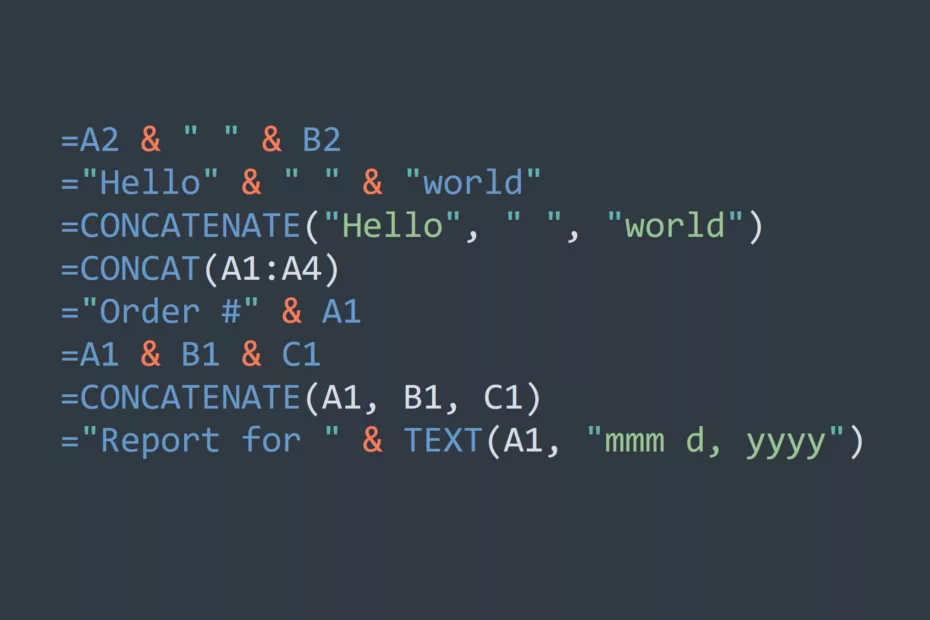
Speed up your work with these Basic Excel Formulas
Excel formulas are essential for organizing, analyzing, and presenting data in a meaningful way. Whether you are an IT professional or a business user, having a good understanding of Excel formulas is important for your success. In this blog post, we will explore some of the most common basic Excel… Read More »Speed up your work with these Basic Excel Formulas